North Korea backed hackers targeting security researchers, Google claims
Attackers would lure security researchers into collaborating via social media and a fake blog.

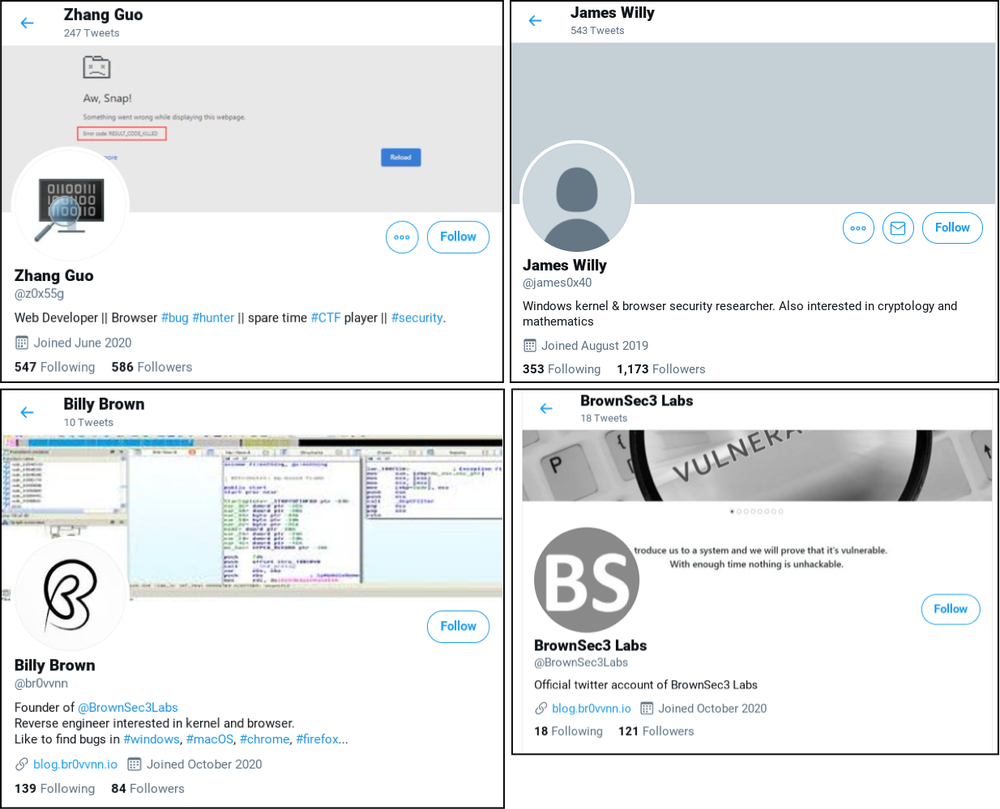
Google has warned security researchers they are being targeted by an ongoing government-backed hacking campaign based in North Korea.
The tech giant said it uncovered several false social media profiles on platforms including Twitter and LinkedIn, where bad actors would lure targets to a fake blog featuring “guest” posts from unwitting legitimate security researchers.
According to Google’s Threat Analysis Group, attackers would then start talking to potential targets, asking if they would like to work together on cyber vulnerability research and use collaboration tools with hidden malware.
In several cases, this allowed perpetrators to install a backdoor on to victims’ computers, even if they were running up-to-date versions of Windows 10 and the Chrome web browser.
“Over the past several months, the Threat Analysis Group has identified an ongoing campaign targeting security researchers working on vulnerability research and development at different companies and organisations,” said Adam Weidemann, from Google’s Threat Analysis Group.
“We hope this post will remind those in the security research community that they are targets to government-backed attackers and should remain vigilant when engaging with individuals they have not previously interacted with.”
In November, the company said that state-backed hackers run by Russia and North Korea had targeted people located in Canada, France, India, South Korea and the US who are “directly involved in researching vaccines and treatments for Covid-19”.
Stuart Reed, UK director of security provider Orange Cyberdefense, said: “This is another example of an attempt by highly sophisticated cyberthreat actors to attack the people that are trying to protect us.
“In the past year we have seen a growing number of such incidents – hackers using social engineering attacks, malware campaigns and a whole host of other tricks to disrupt, misinform, aggravate existing geopolitical tensions and generally spread harm.
“As a result, the emergent threat model has shifted, creating a new normal for cybersecurity professionals trying to temper panic and anxiety with logical, strategic thinking.”





